spear phishing
Many enterprise employees have learned to be suspicious of unexpected requests for confidential information and will not divulge personal data in response to emails or click on links in messages unless they are positive about the source. The success of spear phishing depends upon three things: The apparent source must appear to be a known and trusted individual; there is information within the message that supports its validity, and the request the individual makes seems to have a logical basis.
Spear phishing vs. phishing vs. whaling
This familiarity is what sets spear phishing apart from regular phishing attacks. Phishing emails are typically sent by a known contact or organization. These include a malicious link or attachment that installs malware on the target’s device, or directs the target to a malicious website that is set up to trick them into giving sensitive information like passwords, account information or credit card information.
Spear phishing has the same goal as normal phishing, but the attacker first gathers information about the intended target. This information is used to personalize the spear-phishing attack. Instead of sending the phishing emails to a large group of people, the attacker targets a select group or an individual. By limiting the targets, it’s easier to include personal information — like the target’s first name or job title — and make the malicious emails seem more trustworthy.
The same personalized technique is used in whaling attacks, as well. A whaling attack is a spear-phishing attack directed specifically at high-profile targets like C-level executives, politicians and celebrities. Whaling attacks are also customized to the target and use the same social-engineering, email-spoofing and content-spoofing methods to access sensitive data.
Examples of successful attacks
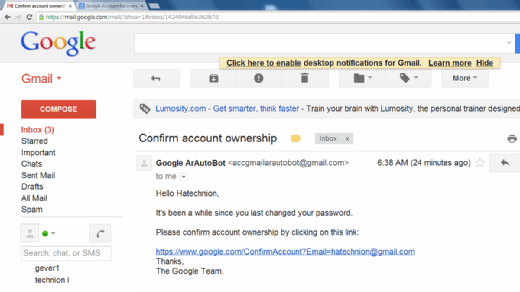
In one version of a successful spear-phishing attack, the perpetrator finds a webpage for their target organization that supplies contact information for the company. Using available details to make the message seem authentic, the perpetrator drafts an email to an employee on the contact page that appears to come from an individual who might reasonably request confidential information, such as a network administrator. The email asks the employee to log into a bogus page that requests the employee’s username and password, or click on a link that will download spyware or other malicious programming. If a single employee falls for the spear phisher’s ploy, the attacker can masquerade as that individual and use social-engineering techniques to gain further access to sensitive data.
CEO fraud
In 2015, independent security researcher and journalist Brian Krebs reported that Ubiquiti Networks Inc. lost $46.7 million to hackers who started the attack with a spear-phishing campaign. The hackers were able to impersonate communications from executive management at the networking firm and performed unauthorized international wire transfers.
CEO fraud is where the attacker impersonates executive staff in a company or corporation to get the employees to fullfill requests without hesitation. These attacks can be hard to spot, and are extremely dangerous when the user falls for the scam. Most CEO fraud attacks ask for money, or to change direct deposit information, etc. It is always best to train users to verify this information by verifying the email by a phone call. Be sure to call known numbers for the person you think it is, and not the numbers in the email.
Spear phishing defense
Spear-phishing attacks — and whaling attacks — are often harder to detect than regular phishing attacks because they are so focused.
In an enterprise, security-awareness training for employees and executives alike will help reduce the likelihood of a user falling for spear-phishing emails. This training typically educates enterprise users on how to spot phishing emails based on suspicious email domains or links enclosed in the message, as well as the wording of the messages and the information that may be requested in the email.